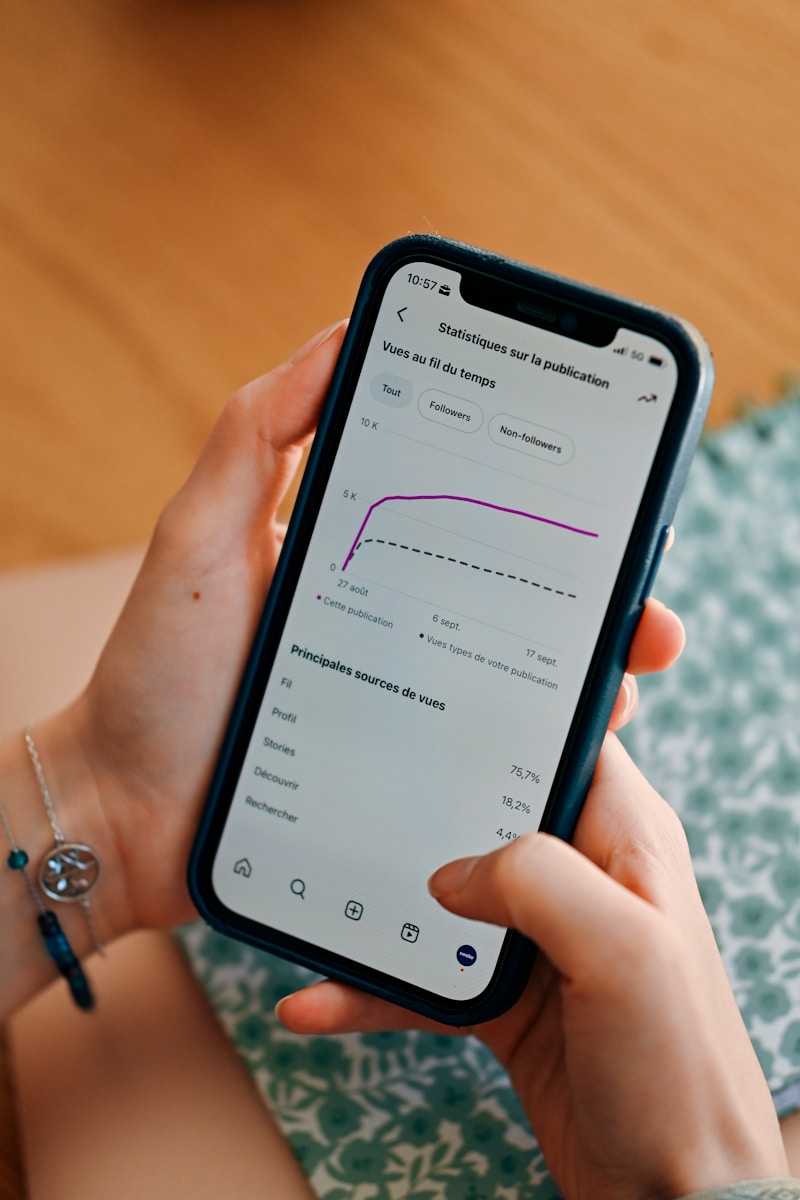
Sovereign rollups – independent execution environments
Implementing self-governing computational strata allows projects to achieve true autonomy by isolating…
Private mempool – transaction privacy protection
To prevent front-running attacks and minimize Miner Extractable Value (MEV), utilizing isolated…
Homomorphic encryption – computation on encrypted data
Encryption methods that allow direct processing of concealed information provide a unique…
State channels – off-chain computation methods
Instant interactions within a decentralized network demand solutions that minimize latency and…
Edge computing – distributed blockchain processing
To optimize data handling and reduce latency, move computation closer to the…
Multisignature schemes – threshold signature systems
Implementing joint authorization mechanisms requires precise management of collective control to enhance…
Proof of space – storage-based consensus
Utilizing hard drive capacity as a mechanism for validating transactions offers a…
Gaming economies – play-to-earn ecosystems
Integrating virtual asset ownership into interactive environments transforms traditional reward mechanisms by…
SNARKs – succinct non-interactive argument systems
Leverage snarks to generate highly compact evidence that verifies knowledge without revealing…
Polynomial commitments – succinct data binding
To ensure integrity and verifiability of polynomial-related information, using cryptographic commitments that…